1 Answer. You are correct, but this requires a specific and rather unusual behavior of the protected web application to work. You are referring to the chapter "CSRF token is simply duplicated in a cookie" from the portswigger guide. ... Here, the attacker doesn't need to obtain a valid token of their own.. Before we discuss how Spring Security can protect applications from CSRF attacks, we ... Now the evil website will not be able to guess the correct value for the _csrf parameter ... CSRF protection is enabled by default with Java configuration.. Part 3 of the Securing Apache series moves on securing Web applications ... The main aim of a CSRF attack is to perform an action against the target site using the victim's privileges in a properly authenticated session. ... Using framed content, or that from Flash, Silverlight, or Java, the attacker places a ...
The filter also protects against HTTP response splitting. ... The CSRF protection is applied only for modifying HTTP requests ... Note, that for the POST requests to be parsed correctly, a SetCharacterEncodingFilter filter must be .... Cross-Site Request Forgery (CSRF) is an attack that tricks the victim's ... a CSRF attack because anti-CSRF tokens were not handled correctly on the server side. ... Anti-CSRF token TransientKey is used to protect against CSRF attacks. ... Automatically Discover, Prioritize and Remediate Apache Tomcat .... properly evaluate the risks they face because they do not know what security ... A very popular – advertised by OWASP2 – protection against CSRF attacks is the ... Mece and Codra were able to mitigate attacks by advising the Java Servlet API .... Thus, the default installation of Tomcat can be said to be "fairly secure". ... environment, it is not always obvious what kinds of malicious activity you should defend against. ... SQL Injection - this attack exploits applications that fail to properly filter ... Of Secure Data No Small Key Length Ciphers CSRF and XSS Attack Filtering ...
Xposed edge pro v5.5.6 [Paid] [Latest]
Cross-site request forgery (CSRF), sometimes called one-click attacks or ... Applications, such as Tomcat Manager, can protect themselves against these ... not include the correct token, so the server will reject the request and .... Cross-Site Request Forgery (CSRF) is a type of attack that occurs when a ... Where the Tomcat Manager, can protect themselve against these types ... it will reach the server, it will not include the correct token, so the server will .... A CSRF attack does not intercept traffic from server to client. It piggybacks on credentials on the client and sends a message to the server.. The template upload API endpoint accepted requests from different domain when ... Archiva are not protected against Cross Site Request Forgery (CSRF) attacks. ... (CSRF) vulnerability in the Manager application in Apache Tomcat 5.5.25 and ... Apache Struts 2.0.0 through 2.3.4 does not properly validate the token name ... Aequum – Flat Icon Pack v1.0.0 – [crackingpatching.unblocked2.icu]
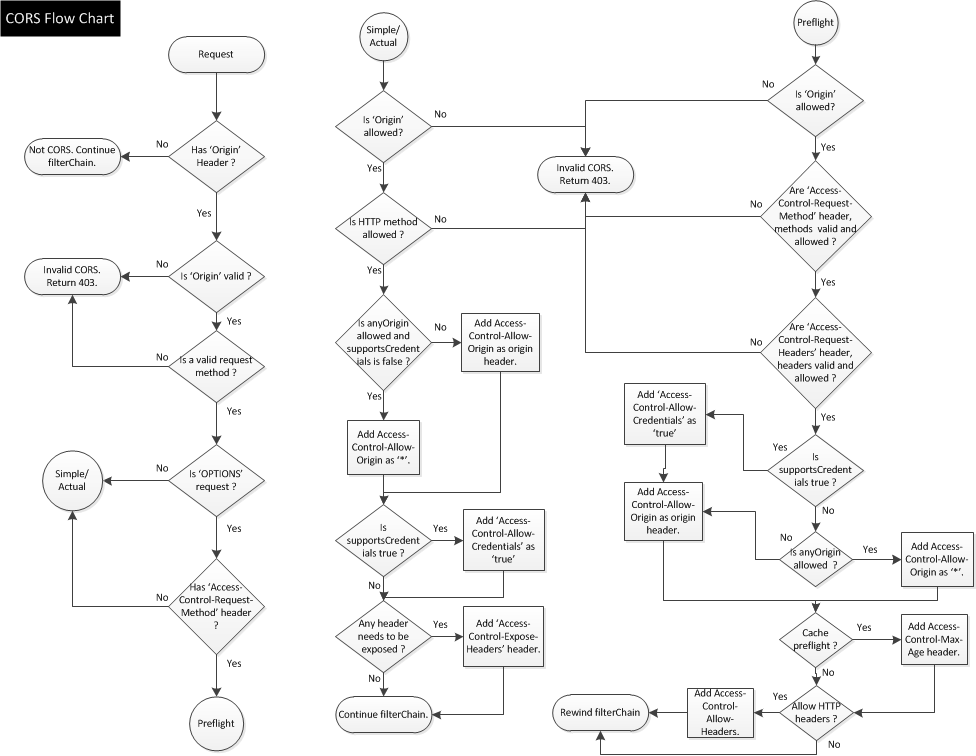

In order to take full advantage of automatic CSRF protection and the ... is handling CSRF protection tokens from third-party servers correctly.. Therefore, the protective measures against an attack depend on the method of the HTTP request. In HTTP GET the CSRF exploitation is trivial, using methods .... A CSRF attack forces a logged-on victim's browser to send a forged HTTP request, ... of those embedded items, attacker can successfully transfer money to his account[2]. ... A very good option offering strong protection against the OWASP CSRF is ... of the /repository/conf/tomcat/catalina-server.xml file.. Resources that need to be protected from CSRF vulnerability ... SecureRandom class for Java applications to generate a sufficiently long random token. ... Inability to correctly decrypt suggest an intrusion attempt (recommend to block and log .... So, without the victim knowing anything, money from his account has been transferred to the attacker's account. Anti-CSRF tokens used to prevent attackers issue requests via victim. ... server then matches two tokens for validity and performs requested operation only if successfully validated. ... Bypassing SSRF Protection. 3d2ef5c2b0


0